This time I played with ThreatMapper (https://github.com/deepfence/ThreatMapper) by deepfence.io
Deepfence ThreatMapper helps you to monitor and secure your running applications in Cloud, Kubernetes, Docker, and Fargate Serverless.
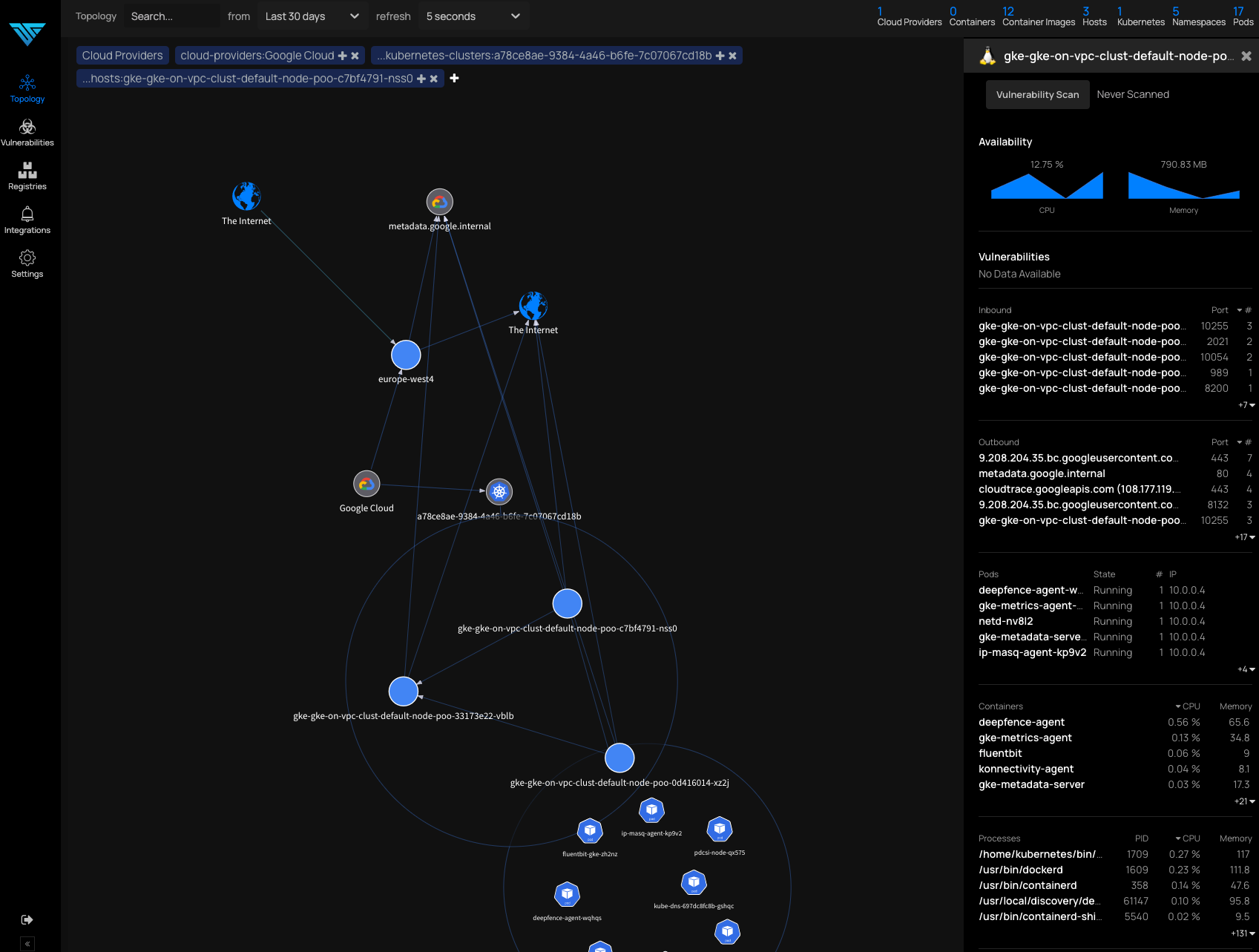
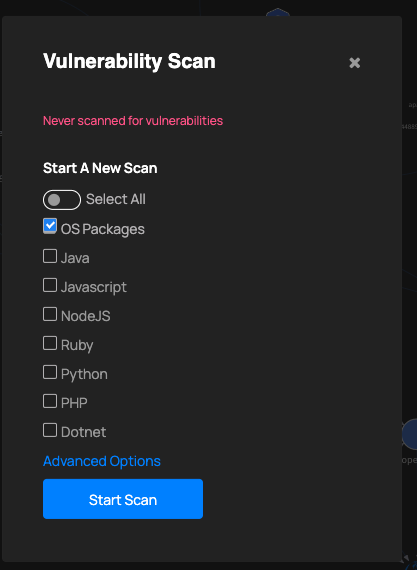
ThreatMapper aims to help you discover running workloads, vulnerabilities and assist with risk assessments of the findings. It was released as open-source on the 13th of October, just four days ago, so the community verdict is still pending.
As I want to test the tools consistently, I have created a terraform module that deploys the ThreatMapper control node on a GCE instance; you can find it here https://github.com/fchyla/threat-mapper-control.
Once you have the control node running, you can deploy sensors on the following platforms.
https://github.com/deepfence/ThreatMapper#deepfence-sensors
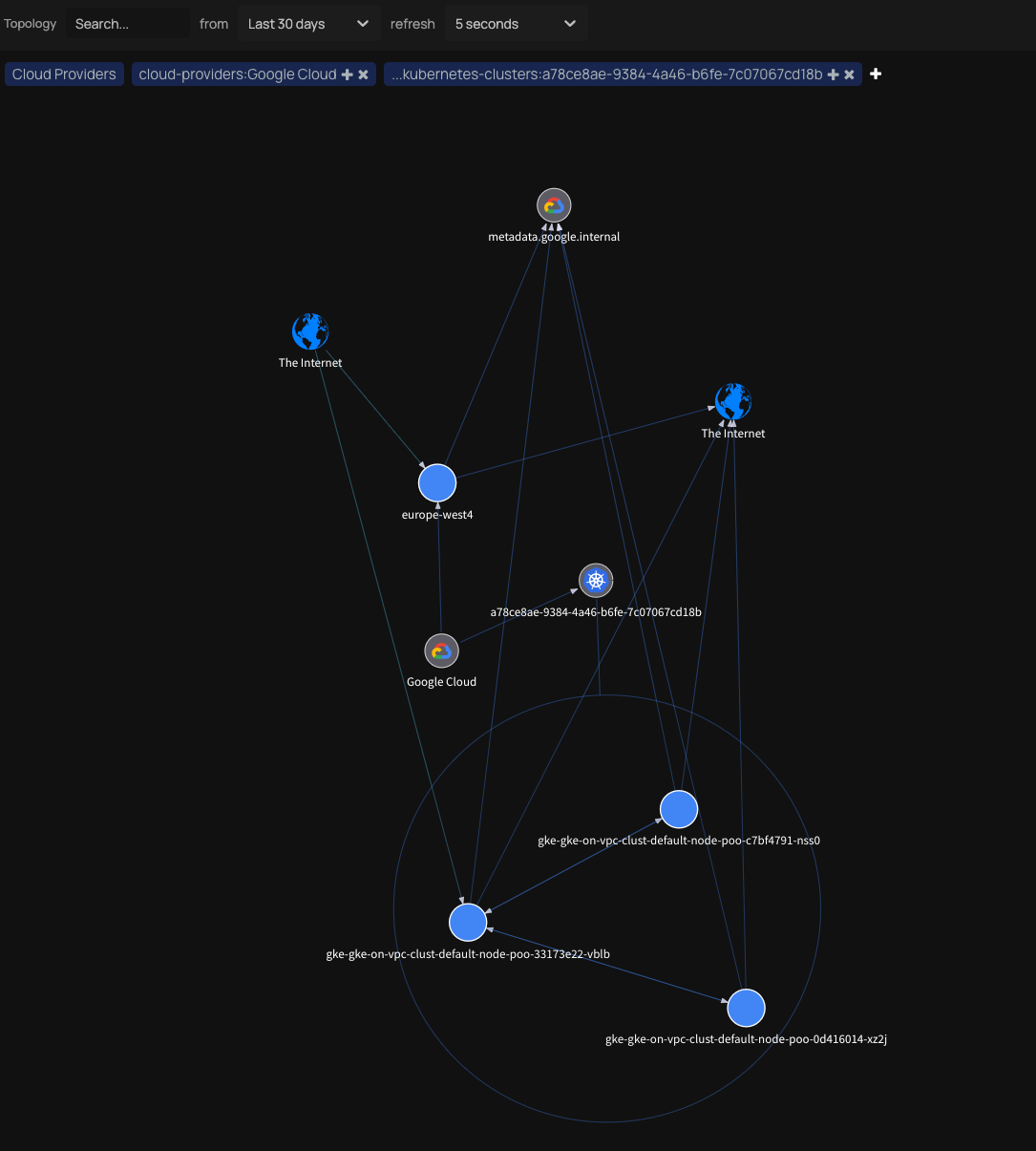
- Kubernetes: You deploy the sensors as a daemonset, similar to other kubernetes services.
- Docker: You deploy the sensors as a docker container on each docker host.
- Bare metal and VM-based platforms: You deploy the sensors in a Docker container on each operating system instance, using a Docker runtime. Both Windows and Linux instances are supported.
- AWS Fargate: You deploy the sensors as a daemon service alongside each serverless instance.
I have managed to deploy the k8s sensors using the provided helm charts; so far, I did not encounter any issues that I could not patch. My terraform deployment includes the fix.
I am looking forward to trying ThreatMapper and reporting back next week!
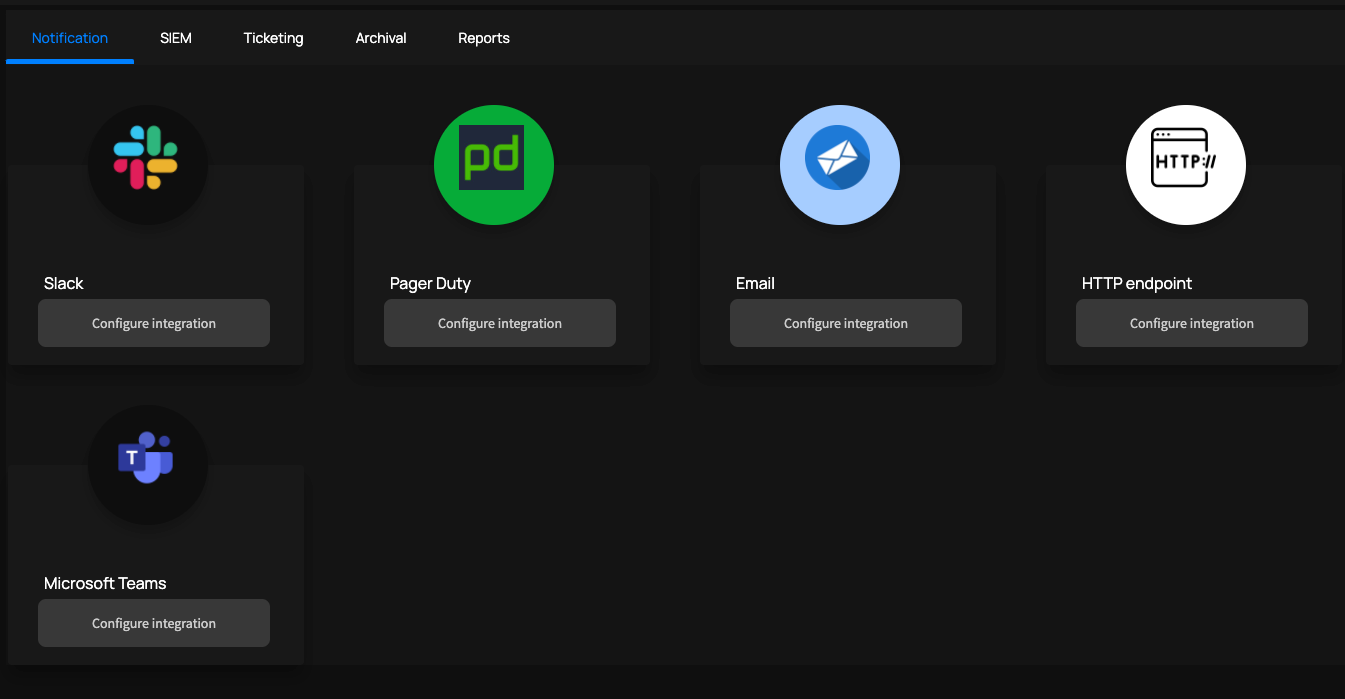
Below you can find some screenshots of the UI with some data.